窃听设备 英文,Introduction to Eavesdropping Devices
时间:2024-10-05 来源:网络 人气:
Introduction to Eavesdropping Devices

Eavesdropping devices, also known as bugs or wiretaps, have been a topic of concern for individuals and organizations alike. These devices are designed to intercept and record conversations without the knowledge or consent of the participants. In this article, we will delve into the world of eavesdropping devices, exploring their types, uses, and the legal implications surrounding their use.
Types of Eavesdropping Devices

There are various types of eavesdropping devices available in the market, each with its unique features and capabilities. Some of the most common types include:
Wireless Bugs: These devices transmit audio signals wirelessly to a receiver, making them difficult to detect. They can be as small as a grain of rice and can be placed in various locations to capture conversations.
Covert Microphones: These microphones are designed to be hidden and can be integrated into everyday objects such as pens, light bulbs, or even clothing. They are often used in corporate espionage or personal surveillance.
Computer Keyloggers: These devices are installed on computers to record keystrokes, capturing sensitive information such as passwords and credit card numbers.
Cell Phone Tap: This device intercepts and records phone calls made on a specific cell phone. It can be used to monitor the activities of an individual or to gather intelligence.
How Eavesdropping Devices Work

Eavesdropping devices work by capturing audio or digital signals and transmitting them to a receiver. The process typically involves the following steps:
Signal Capture: The device captures audio or digital signals through a microphone or other sensor.
Signal Processing: The captured signals are processed and converted into a format suitable for transmission.
Transmission: The processed signals are transmitted wirelessly or through a wired connection to a receiver.
Reception and Decoding: The receiver captures the transmitted signals and decodes them back into audio or digital format for playback or recording.
Legal Implications of Using Eavesdropping Devices

The use of eavesdropping devices is heavily regulated by law, and unauthorized use can lead to serious legal consequences. In many countries, it is illegal to use eavesdropping devices without the consent of all parties involved in the conversation. The following are some of the legal implications of using eavesdropping devices:
Privacy Violation: Unauthorized eavesdropping is a violation of privacy rights and can lead to civil lawsuits.
Penalties: In some jurisdictions, the use of eavesdropping devices can result in fines, imprisonment, or both.
Legal Defense: If you are a victim of eavesdropping, you may have legal remedies available to you, such as seeking damages or an injunction against the perpetrator.
Preventing Eavesdropping
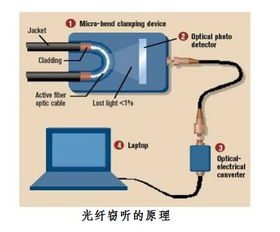
To protect yourself from eavesdropping, it is important to be aware of the risks and take appropriate precautions. Here are some tips to help prevent eavesdropping:
Secure Your Communication Channels: Use encrypted messaging apps and secure communication methods to protect your conversations.
Be Mindful of Your Surroundings: Be cautious of your surroundings when discussing sensitive information in public places.
Use Countermeasures: Employ counterintelligence techniques, such as bug sweeping, to detect and eliminate eavesdropping devices.
Consult with Experts: If you suspect that you are being eavesdropped upon, consult with a professional to assess the situation and take appropriate action.
Conclusion

Eavesdropping devices are a serious threat to privacy and security. Understanding the types, uses, and legal implications of these devices is crucial for individuals and organizations alike. By being aware of the risks and taking appropriate precautions, you can help protect yourself from unauthorized surveillance and ensure the confidentiality of your communications.
Tags: EavesdroppingDevices WirelessBugs CovertMicrophones ComputerKeyloggers CellPhoneTap LegalImplications PreventingEavesdropping Privacy Security

相关推荐
教程资讯
教程资讯排行